Proxy Server Firewall: Maximum Security for Your Network
Proxy server firewall offers a highly secure firewall solution for on-premises networks. Operating similarly to proxy servers, they isolate internal network assets from external internet threats. Like conventional firewalls, proxy server firewall filter traffic to safeguard against cyber threats. Additionally, they possess the capability to block access to specific websites when necessary.
While proxy server firewall presents several key advantages, they also come with certain limitations. This article will explore how proxy server firewall functions and their role in enhancing network security.
What Is a Proxy Server Firewall?
A proxy server firewall enhances network security by restricting the applications a network can support, which while boosting security, may impact functionality and speed. This type of firewall represents the pinnacle of secure network barriers, filtering communications at the application layer to safeguard network resources.
Traditional firewalls lack the capability to decrypt traffic or scrutinize application protocol traffic. They often rely on an intrusion prevention system (IPS) or antivirus solutions to fend off threats, which only address a limited portion of the vast threat landscape that organizations now encounter.
In contrast, a proxy server firewall serves as a critical intermediary between computers and servers on the internet, securing data as it enters and exits a network. It evaluates traffic to determine permissible interactions, scans incoming data for potential cyber threats or malware, and employs caching, filtering, logging, and control measures on requests from devices. This ensures that networks remain secure and impenetrable to unauthorized access and cyberattacks.
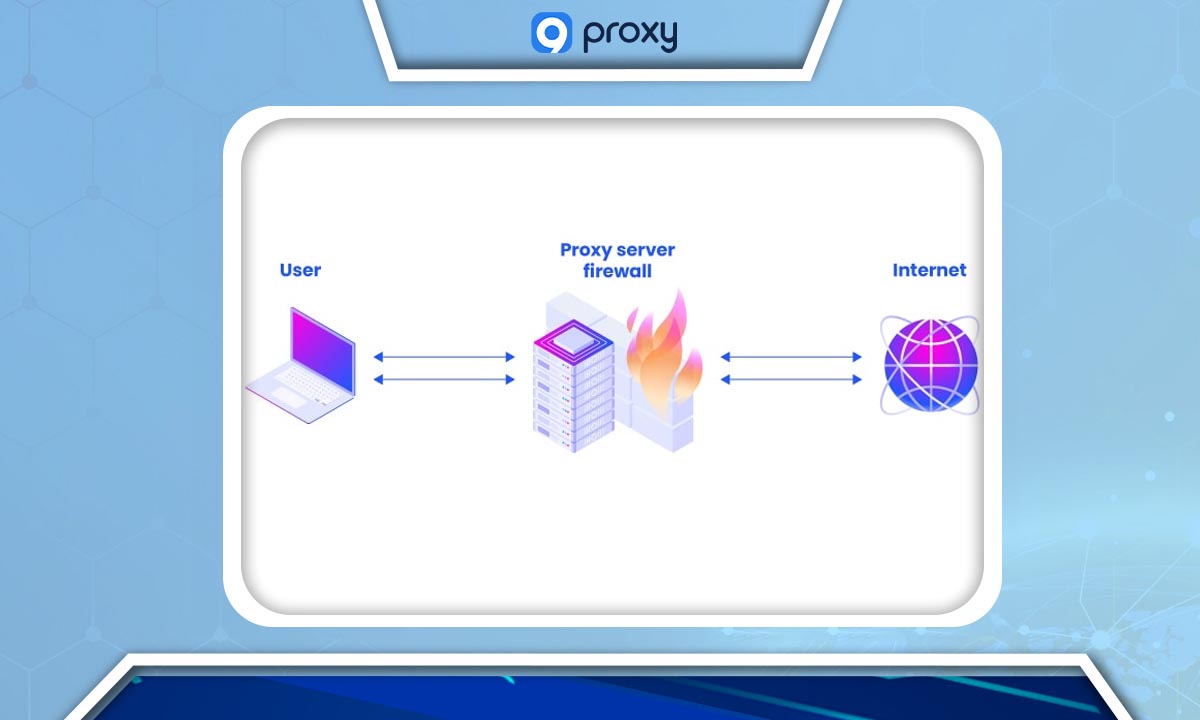
How Do Proxy Server Firewalls Work?
A proxy server firewall functions as a vigilant gatekeeper, mediating between an organization's internal network and external services such as the public internet. It acts on behalf of users, initiating connections to requested services, scrutinizing the traffic for security risks, and ensuring adherence to established network policies.
Deep Packet Inspection (DPI) is a key technique used, delving into the details of incoming data packets to identify and thwart unauthorized access, significantly bolstering the network’s defenses against potential intrusions.
At its core, the proxy intercepts internet requests originating from within the network, evaluates them based on the organization's security protocols, and if deemed safe, facilitates communication with the desired external service. After processing, the firewall relays the service’s response back to the requester, effectively concealing the internal network's specifics from the outside world.
This method effectively blocks direct interactions between internal users and external services, thus securing the network against unauthorized breaches and providing a degree of anonymity by shielding internal internet protocol (IP) addresses. This is particularly crucial when accessing web-based services, as it ensures that only secure, authorized content is delivered back to the user.
The proxy firewall's prowess in inspecting and controlling data at the application layer makes it a formidable defense against advanced cyber threats, such as malware and phishing attacks, earning it the moniker of an application firewall. It is also invaluable as a server firewall. Its central role in implementing rigorous network security measures is indispensable, particularly in complex enterprise settings where meticulous control over data flow is essential.
Moreover, proxy firewalls enhance network efficiency by caching content to speed up load times, compressing data to optimize bandwidth usage, and even restricting access to certain websites.
Advantages and Disadvantages of Proxy Server Firewall
Proxy firewalls serve as critical intermediaries between end users and the internet, meticulously inspecting and regulating traffic according to predefined rules. The following outlines the primary benefits and potential drawbacks associated with the use of a proxy firewall:

Advantages
The primary function of a proxy firewall is to establish a centralized point of access, which facilitates comprehensive threat assessment of application protocols, effective threat detection, and validation of network traffic. This central access point allows for precise control over the firewall settings, enabling organizations to tailor the firewall to their specific network requirements and corporate policies.
Moreover, a proxy firewall blocks direct connections between a user’s computer and external websites. This configuration significantly enhances network security by performing in-depth inspections of every data packet entering and exiting the network. As a result, organizations are better equipped to thwart sophisticated and high-risk malware attacks, ensuring a highly secure network environment.
Disadvantages
Despite its robust security enhancements, a proxy firewall also introduces certain limitations. A notable drawback is the need for the firewall to establish a new connection for each packet transferred, which can create a bottleneck in the flow of traffic. This often leads to a noticeable slowdown in network performance and introduces a single point of failure that could be exploited. Additionally, some proxy firewalls may support only specific network protocols, restricting the range of applications that can be effectively secured by the network.
Comparing Proxy Server Firewalls and Traditional Firewalls
Proxy server firewalls and traditional firewalls are both important for keeping your network safe, but they work in different ways. A proxy server firewall acts like a middleman, checking and passing along requests between your internal network and the internet. This lets it inspect the content more closely and hide your internal IP addresses, boosting both privacy and security.
Traditional firewalls, on the other hand, work by checking IP addresses and ports at the network or transport layers. They can block or allow traffic based on set rules, but they don't look as deeply into the content of the data packets as proxy firewalls do. Because of this, while traditional firewalls provide basic protection, they can't analyze content or adjust controls as finely as proxy firewalls.
A big plus for proxy firewalls is their ability to store data temporarily (caching), which can speed up your network. Traditional firewalls don't offer this benefit since they focus only on who gets in and out. However, the detailed checking by proxy firewalls can slow down your network because of the extra time it takes to process everything, which is usually not an issue with traditional firewalls.
Benefits of Usin g a Proxy Server Firewall
Opting for a proxy server firewall over a traditional one comes with several significant advantages that enhance network security and management.
Enhanced Security Measures
Proxy server firewalls are considered among the safest due to their method of operation. They prevent a direct connection between your network's internal resources and external threats. Any attacker must first get through the proxy, which serves as a robust gatekeeper. Additionally, proxy servers disguise IP addresses, making it difficult for attackers to pinpoint and target network devices.
Most notably, proxy firewalls combine this isolation with advanced traffic filtering capabilities. Through Deep Packet Inspection, they meticulously examine each piece of incoming data, enabling them to catch unauthorized access more effectively than traditional firewalls that might only scan packet headers.

Comprehensive Auditing and Logging Capabilities
Proxy gateways do more than just inspect incoming and outgoing data; they meticulously log these interactions. This can include detailed records of network addresses, destination ports, and source IP addresses, among other data points. These logs are crucial for tracking and analyzing network activity, helping to identify and respond to potential security incidents more swiftly.
In-depth Threat Analysis for Secure Networks
By acting as a secure intermediary between your internal networks and the public internet, proxy servers provide a controlled environment for security teams to conduct thorough threat analyses. This setup allows for the testing of security policies and the quarantine of potential threats without risking the integrity of the main network resources.
Improved Management of Network Traffic
Proxy server firewalls offer refined control over network traffic, allowing organizations to implement detailed security policies tailored to different applications and user roles. This capability is enhanced by the logging features, which help monitor and track user behavior effectively.
Additionally, proxies help manage overall network traffic. They can cache frequently accessed web pages, alleviating network congestion. Web filtering features can also block access to non-work-related sites like social media, boosting workplace productivity.

Selecting an Appropriate Proxy Server Firewall System
Choosing the right proxy server firewall for your network involves thoughtful planning, as it might not always be the best fit for every organization's architecture.
Proxy firewalls are especially beneficial for environments with a large on-site workforce, such as schools or universities, where controlling and filtering internet traffic is crucial. However, for organizations with a predominantly remote workforce, remote access firewalls might be more effective. Similarly, cloud firewalls are preferable for companies heavily utilizing Software-as-a-Service (SaaS) applications.
If you decide to go ahead with a proxy firewall, here are some key challenges to consider:
- Ease of Use: Proxy firewalls can be complex to configure and manage. If a proxy is too restrictive or difficult to use, it may lead to users bypassing the system, which defeats its purpose. Ensuring that the proxy firewall is user-friendly is essential, especially when scaling up.
- Speed: While all proxies inherently reduce network speed to some extent due to their filtering processes, choosing a proxy with efficient traffic management is critical. A poorly designed proxy can lead to network bottlenecks, exacerbating issues like DDoS attacks and reducing overall network performance.
- Redundancy: Because proxy servers can become single points of failure, their malfunction can lead to significant downtime or security breaches. It's advisable to integrate proxies with other security systems to maintain continuous protection and network availability.
- Cost: Proxy server firewalls are often more costly than other types of firewalls. Implementing a proxy solution should be based on a clear business case that justifies the investment by demonstrating tangible benefits to your network security and management.
FAQ
What are the limitations of a proxy server firewall?
Proxy server firewalls can slow down network traffic due to the thorough inspection and processing of data packets, leading to bottlenecks if not properly scaled. They require skilled IT personnel for management and setup, potentially increasing operational costs.
Can a proxy server firewall handle encrypted traffic?
Yes, modern proxy server firewalls can handle encrypted traffic, such as HTTPS. They are equipped with SSL inspection capabilities, allowing them to decrypt, inspect, and re-encrypt traffic. However, this process may introduce some latency.
Conclusion
In conclusion, everyone online faces potential cyber threats. As technology advances, completely avoiding cyberattacks has become increasingly challenging. Businesses lacking effective security measures risk losing sensitive data and may face restrictions when accessing certain websites for data collection, hindering employee productivity.
Fortunately, proxy server firewall offers the robust protection needed for safe data gathering. By investing in the right firewall solution, businesses can not only protect their data but also stay competitive by collecting information more efficiently than their rivals.
Get Newsletters About Everything Proxy-Related